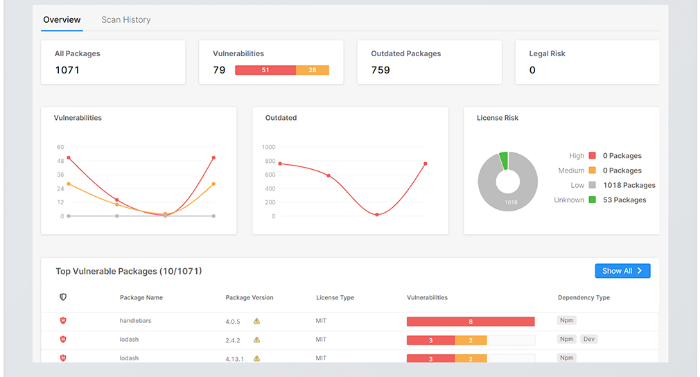
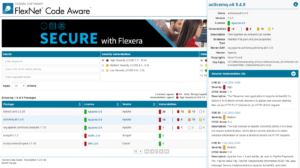
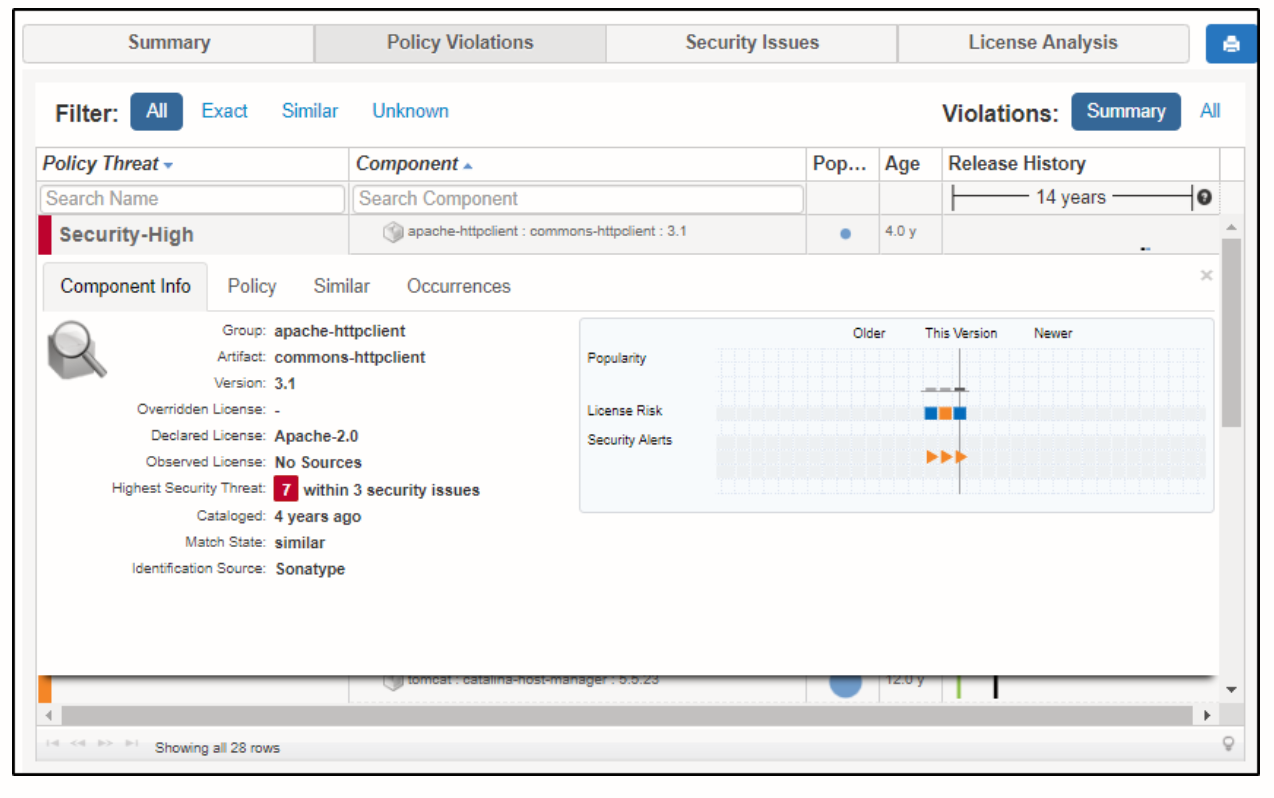
Snyk Security - Code, Open Source, Container, IaC Configurations - IntelliJ IDEs Plugin | Marketplace
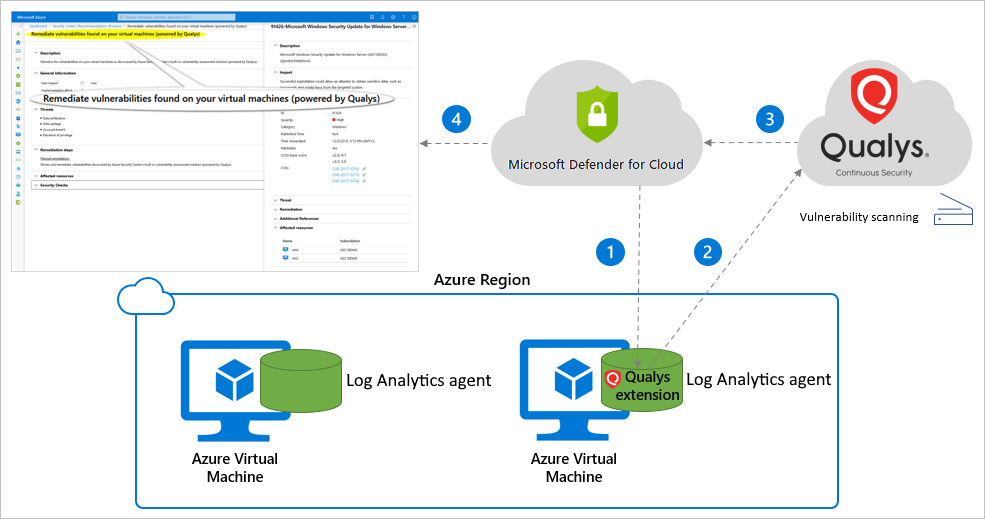
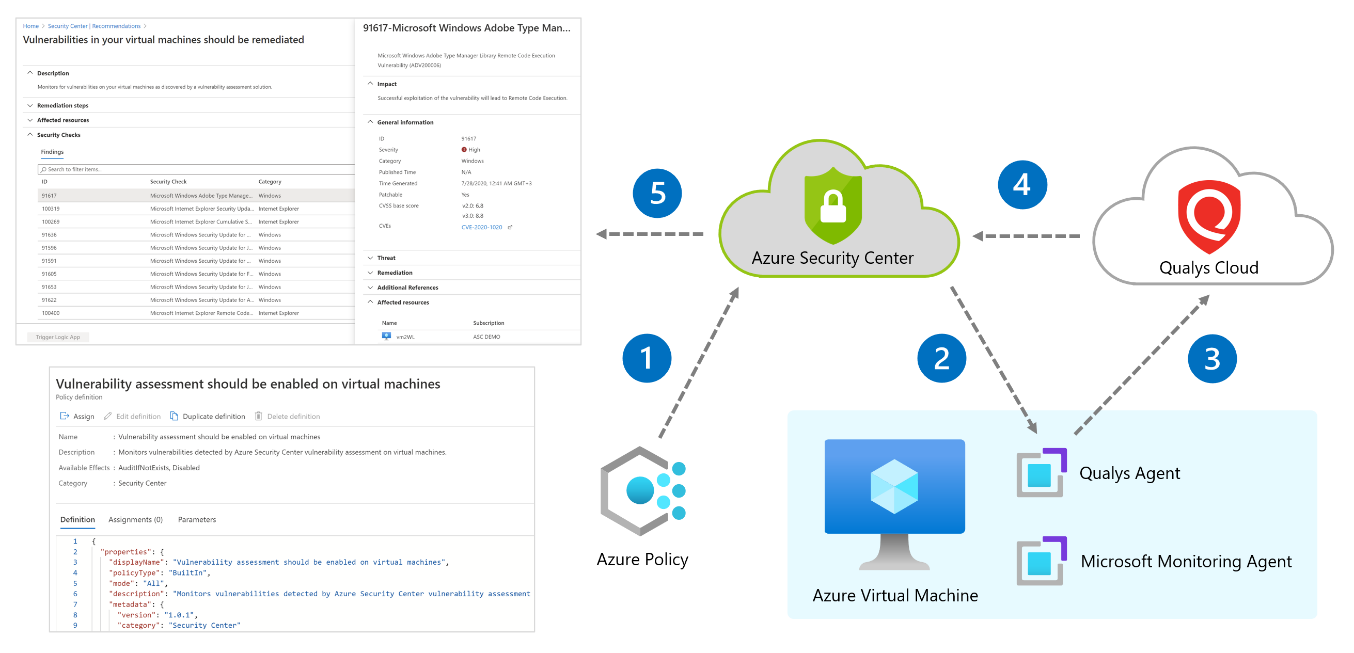
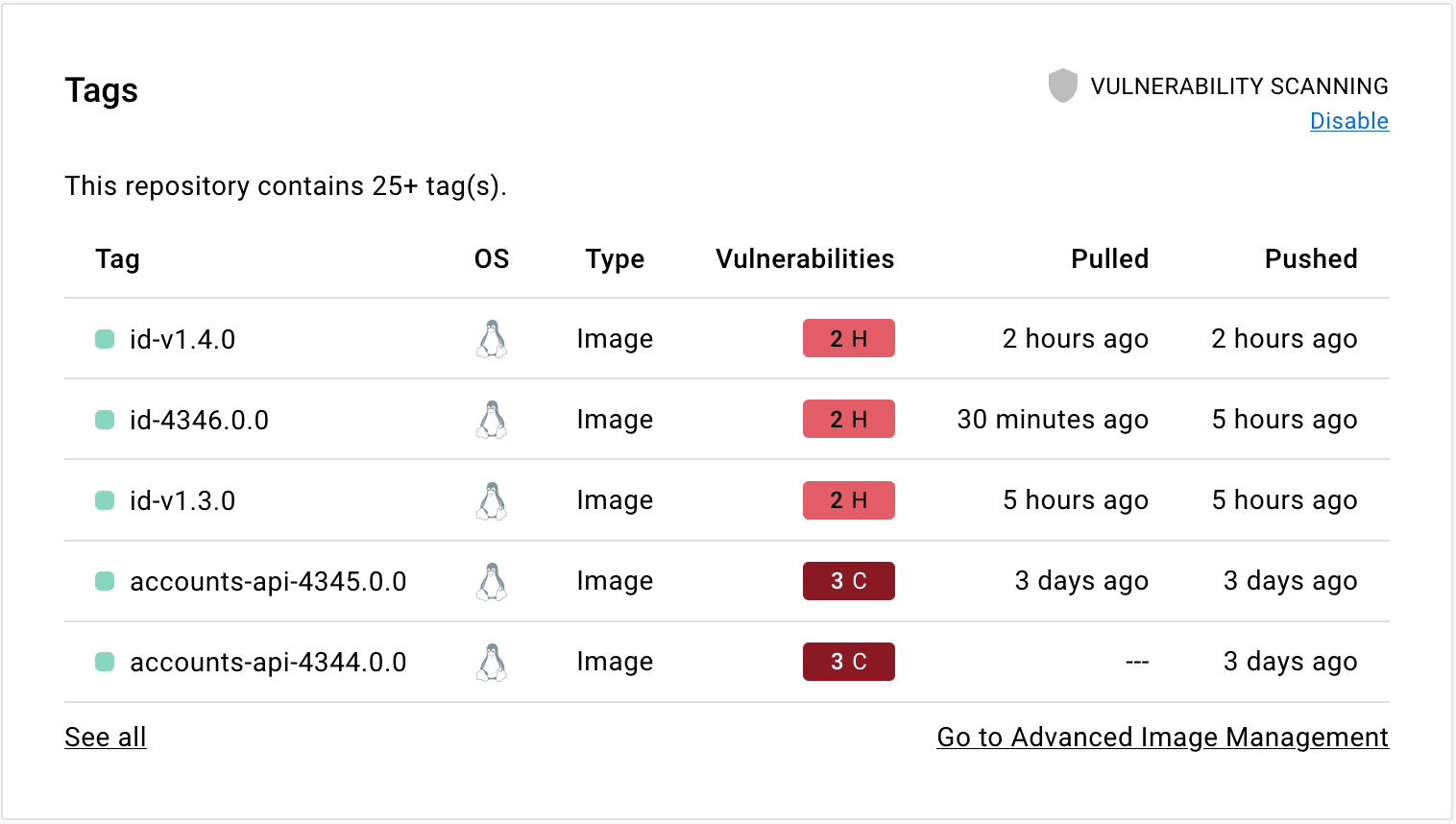
Defender for Cloud's integrated vulnerability assessment solution for Azure, hybrid, and multicloud machines | Microsoft Docs

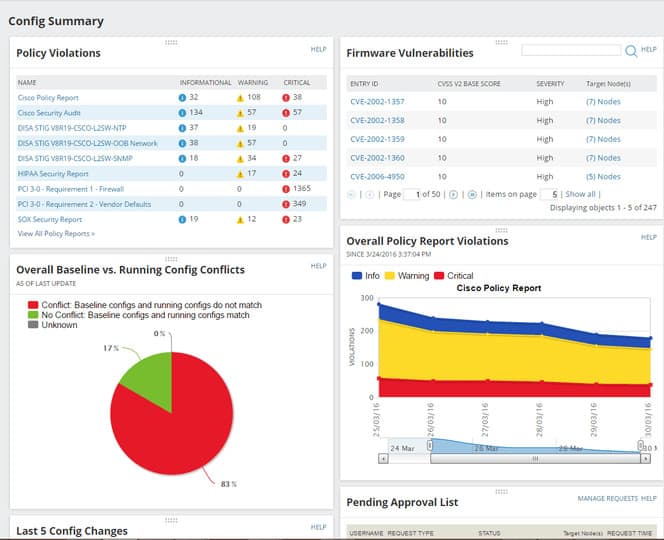
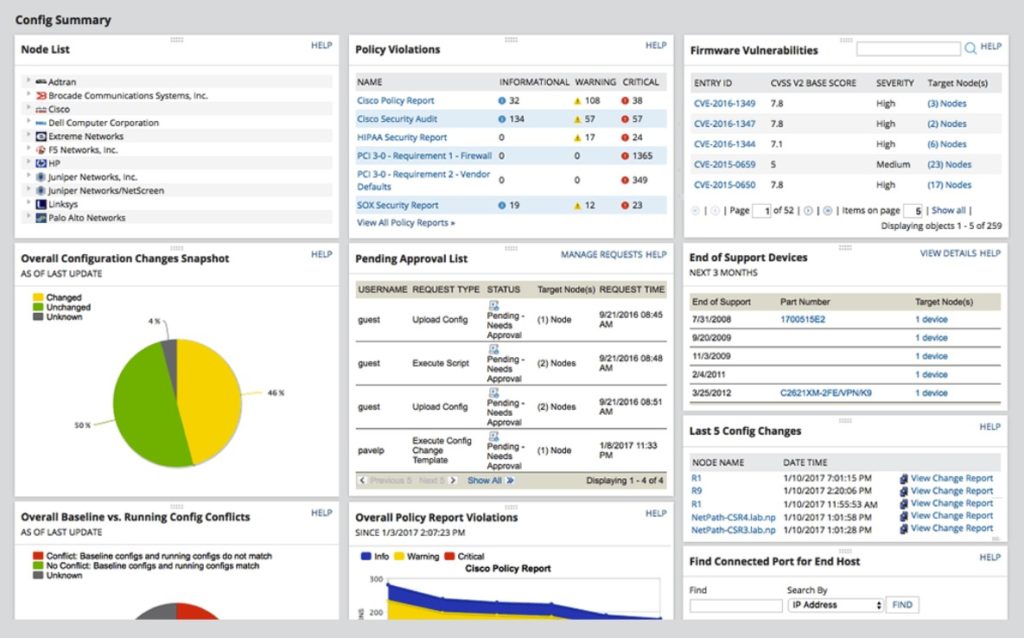
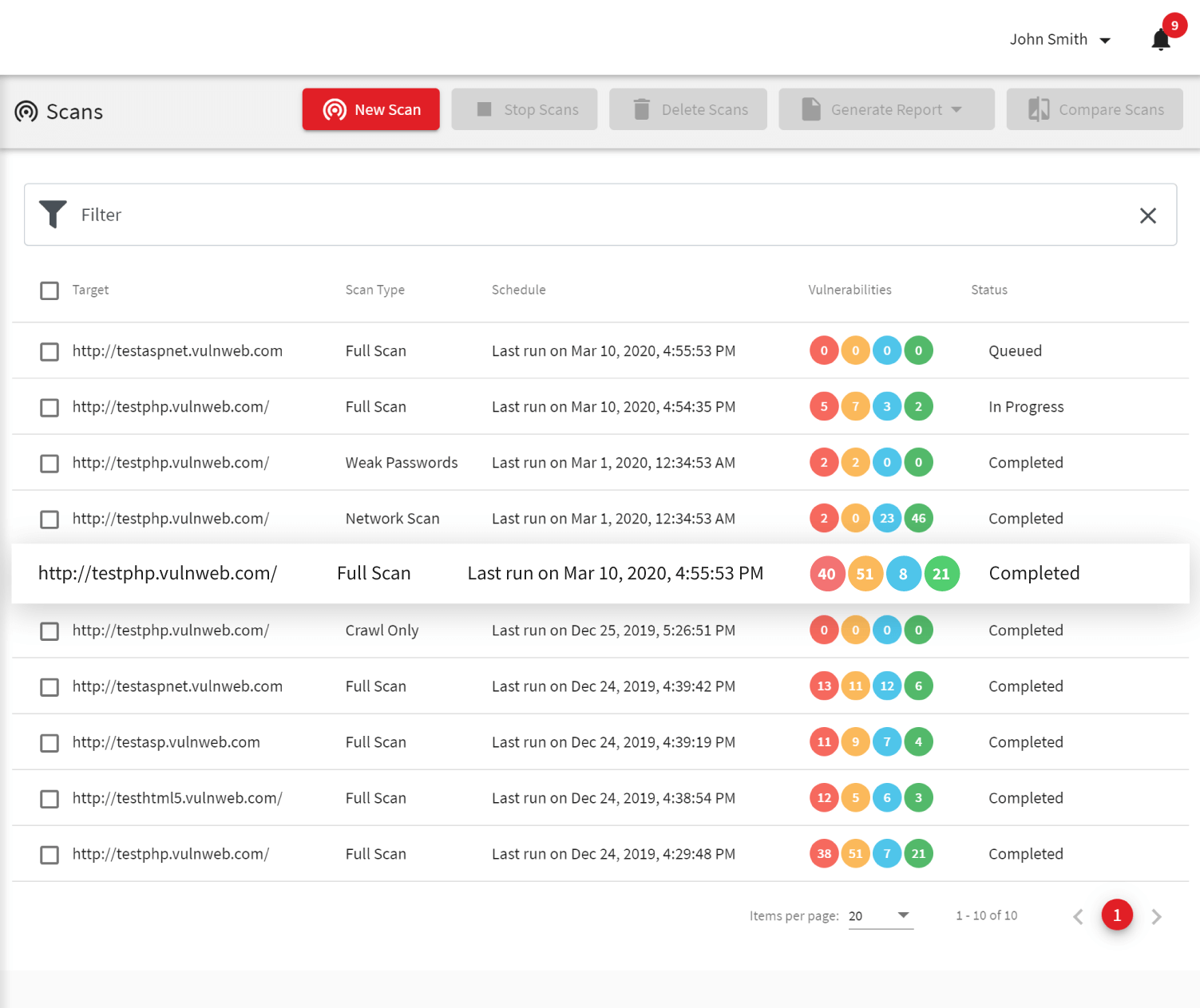
Vulnerability Assessment Tool | Security Vulnerability Assessment - ManageEngine Vulnerability Manager Plus
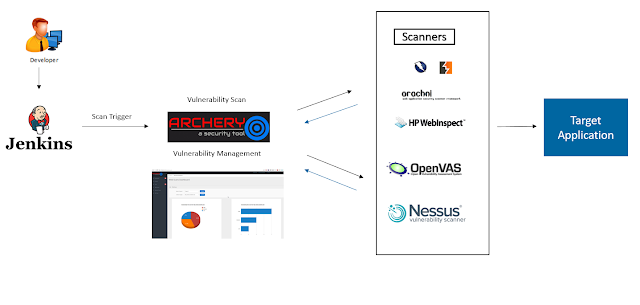
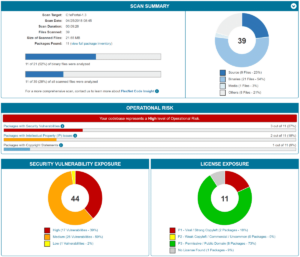
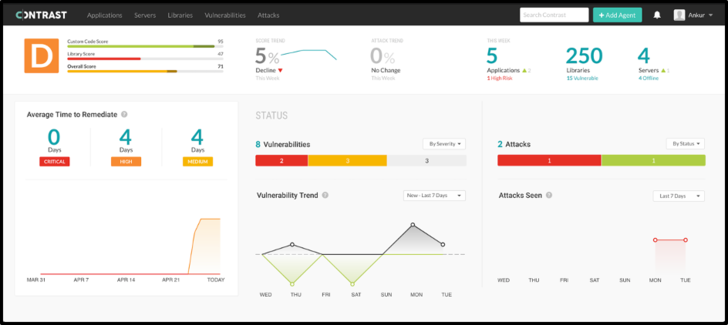
Archerysec - Open Source Vulnerability Assessment And Management Helps Developers And Pentesters To Perform Scans And Manage Vulnerabilities - Hacking Land - Hack, Crack and Pentest